I wrote new ebook about AppleScript security (in Japanese).
PDF 562 pages and Zip archive.
https://piyomarusoft.booth.pm/items/7619827
AppleScript — a powerful automation language that can freely access various macOS features and interact with GUI-based applications — can be distributed as run-only scripts or applets whose source code cannot be viewed.
Even when such scripts are saved in a run-only format that appears to be “encrypted,” they are actually stored as a sequence of instructions known as Apple Events Code. Text strings within these codes can be extracted by using terminal commands such as hexdump or strings.
In recent years, tools have emerged that can dump Apple Events Code itself—visualizing its internal instruction structure. Although these tools were originally developed for defensive analysis, they are equally accessible to potential attackers.
This book provides a detailed examination of what kinds of information can be extracted through Apple Events Code dumping tools and how such information appears in practice. Based on these findings, it outlines potential risks and preventive measures, serving as a foundational guide for the secure use of AppleScript.
Table of Contents
Chapter 1 — Is “Run-Only” Really Safe?
Overview and scope of AppleScript functions; Spread of executable programs; Function limitations imposed by system settings; Information obtainable through hex and string dumps; Reference materials related to Apple Events.
Column: Syntax highlighting settings for the AppleScript listings in this book.
Chapter 2 — Structure of an AppleScript Applet
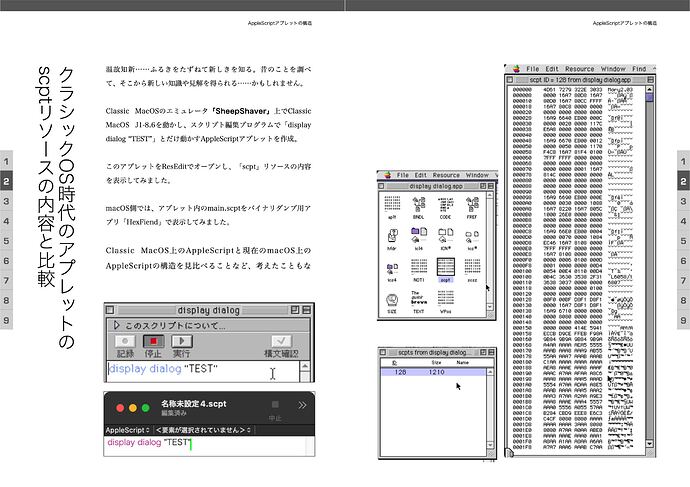
Creating applets with Script Editor; Exploring the internal structure of exported applets; Comparison with scpt resources from the classic MacOS era.
Chapter 3 — Extracting Information through Apple Event Dumps
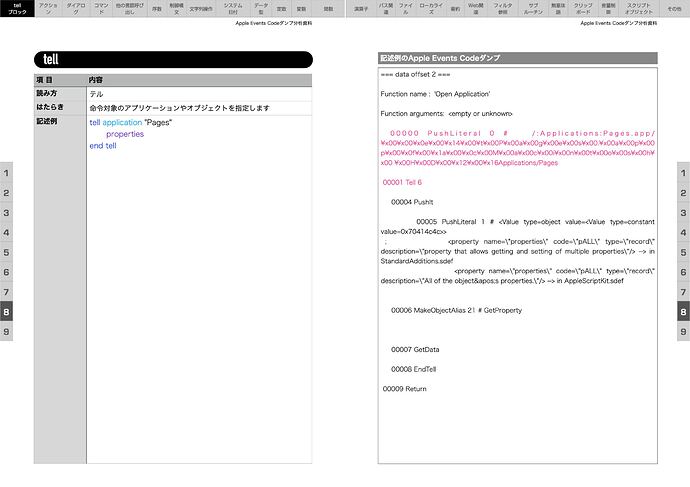
Complete decompilation of AppleScript is impossible; Interpreting Apple Events Code for readability; Tools such as applescript-disassembler, aevt_decompile, and the integrated analysis tool as_disassem+decompile; Using strings and hexdump.
Chapter 4 — The Reality of Information Leakage from Run-Only Scripts
How each data type appears in Apple Events Code; Testing by changing program complexity; Alphabetic and numeric strings; Japanese text; Emoji strings; Boolean, integer, and floating-point values; date objects; Lists (arrays) of numbers and strings; Records; Application objects; AppleScriptObjC apps developed in Xcode.
Chapter 5 — Technical Methods to Prevent Information Leakage
Writing usernames and passwords in forms not visible to simple dumps; Using keychain storage still requires access keywords; Fundamentals of data encryption — (1) Shift ciphers, (2) Substitution ciphers with cipher tables, (3) Polyalphabetic ciphers and key systems (Vigenère cipher), (4) Modern encryption with OpenSSL for secure and automatic key handling; Program obfuscation — (1) Data format alteration, (2) Variable name replacement with emoji, (3) Structural complication.
Chapter 6 — Design Guidelines for Safe Distribution
Distribution formats of AppleScript and levels of required effort; Code signing as a minimum requirement and the necessity of developer registration; Online applet distribution as practical experience.
Chapter 7 — Rethinking AppleScript Security
Recent AppleScript-related problems caused by memory leaks; Risks of storing usernames, passwords, or API keys in plaintext within scripts; Inter-application communication interception once possible but now restricted; Risks of network-based operations being intercepted; AppleScript execution tools that save embedded scripts in plaintext configuration files.
Chapter 8 — Reference Materials: Apple Events Code Dump Analysis
Run-only Apple Events Code dumps of example scripts that include all reserved words.
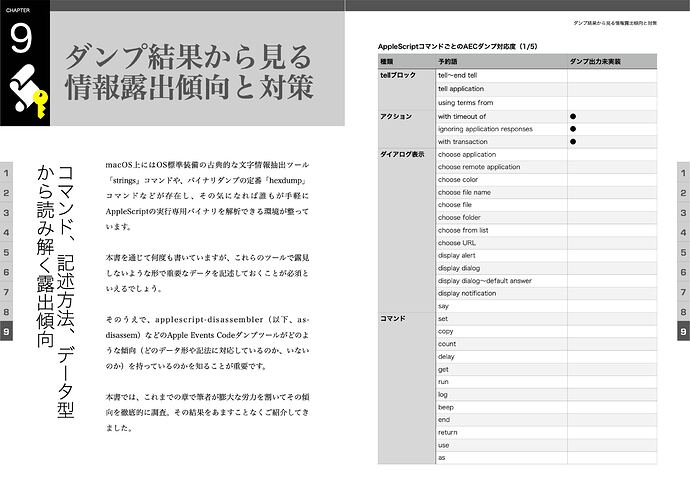
Chapter 9 — Exposure Trends and Countermeasures Observed in Dump Results
Exposure trends analyzed through commands, syntax, and data types; Effectiveness of script object as a countermeasure against dumps; Security practices in AppleScript reconsidered through the “OSAMiner incident.”
Column: AppleScripts created and used in compiling this book.